Digital Security Information
The material was prepared using the original video and text available in Russian at the following links: https://www.youtube.com/watch?v=QLACSL_eyuk, https://mailchi.mp/getkit.news/readnews
Digital security – or how to protect your online identity, data, and other assets?
Activists, human rights defenders and civil society organizations are at risk of violation of their right to information and freedom of expression.
In this section, find practical advices on how to protect your digital information.
First of all, you should answer the following questions for yourself and assess your risks
- What do I want to protect?
(In case I want to protect, for example, document scans, and not communication, then the recommendation to use Signal will not be relevant)
- Where is information stored?
(on a computer, in the office, at home, on which messenger, on which platform?)
- Who has access to information?
(shared computers, folders, directories, you should specify what is important and what can happen to information. The answer is subjective)
- What can happen to it?
(cases of phishing or account hacking attempts…)
- What will be the consequences for ME?
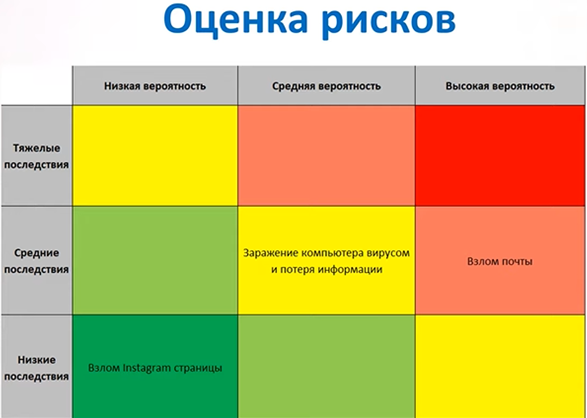
If you have high risks
- Seek help from colleagues, donors, community, organizations
- Request an audit or assessment of your risk exposure
Digital hygiene
- Messengers are better than SMS
- Unique passwords for important accounts
- Two-factor authentication on important account
- Learn to recognize phishing
- Backup copies of important information
- Encrypt and lock devices
- Update all programs
- Uninstall programs you don’t use
How often are accounts hacked?
- An attacker has learned your password from a hacked site and tries to log into Facebook with this password
- Phishing – a fake site asks you to enter your password or two-step verification code
- Your account has junk mail, an attacker has gained access to it and is trying to reset passwords on your other accounts
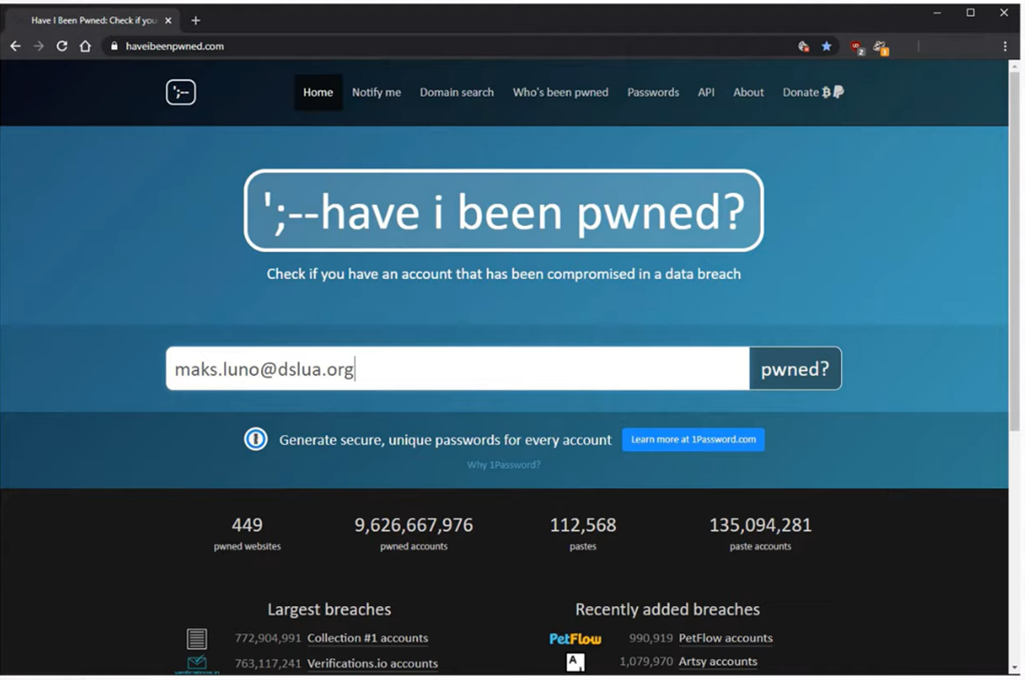
Check your email with https://haveibeenpwned.com/
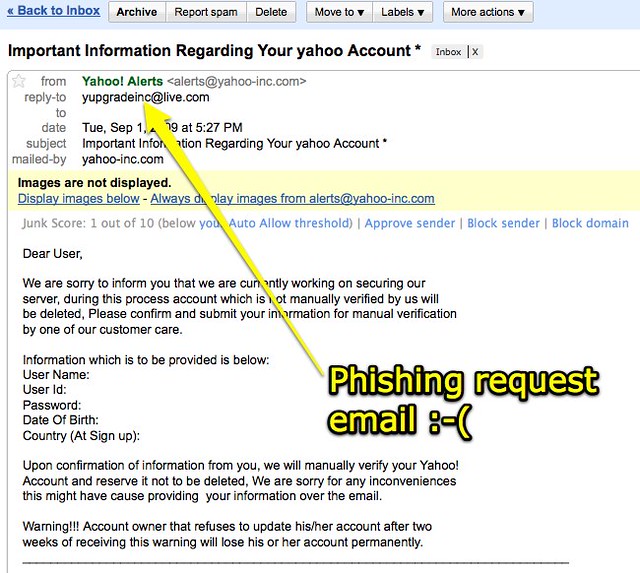
Phishing message
Phishing is when attackers send malicious emails designed to trick people into falling for a scam. The intent is often to get users to reveal financial information, system credentials or other sensitive data.
What Does a Phishing Email Look Like?
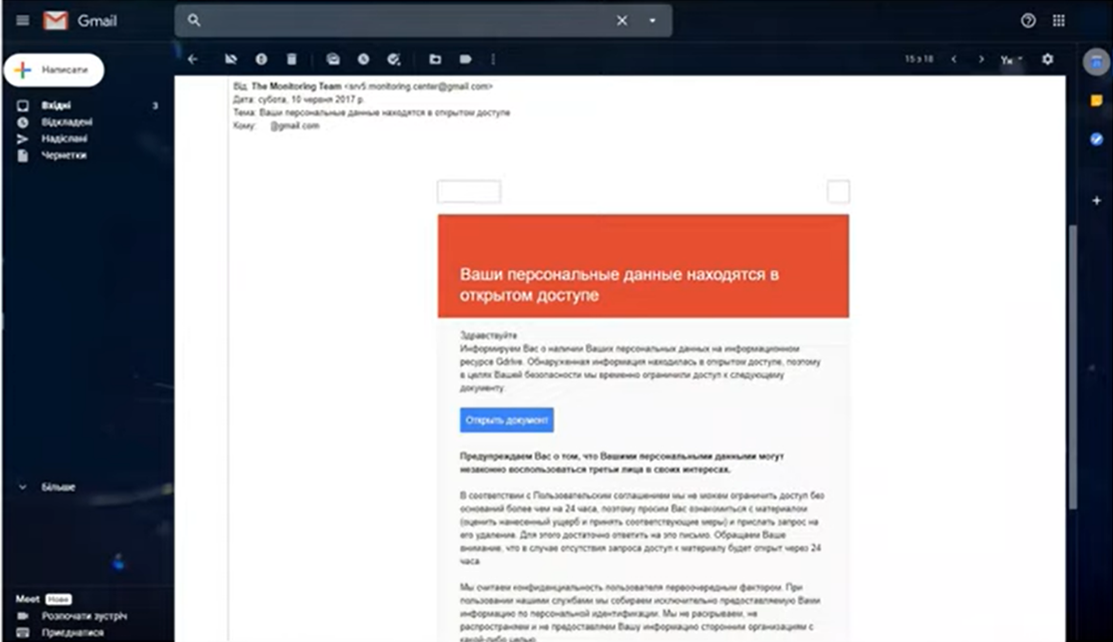
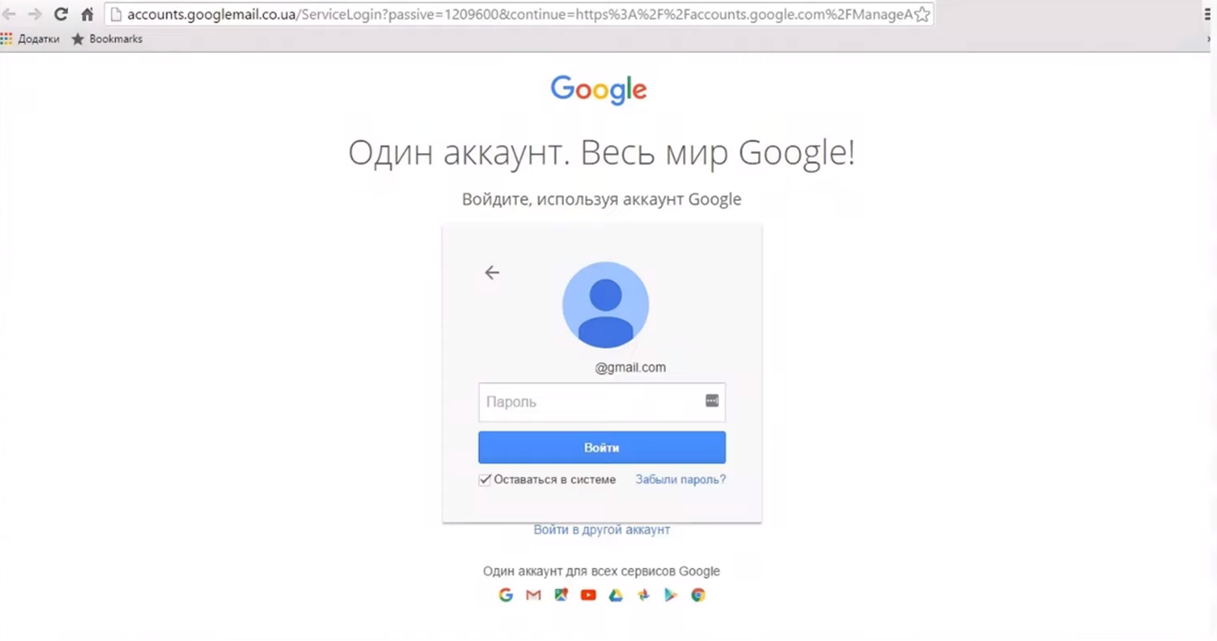
Takes you to a page which looks identical to Google, Apple or other official landing pages, in order to get your password.
Example of a fake landing page:
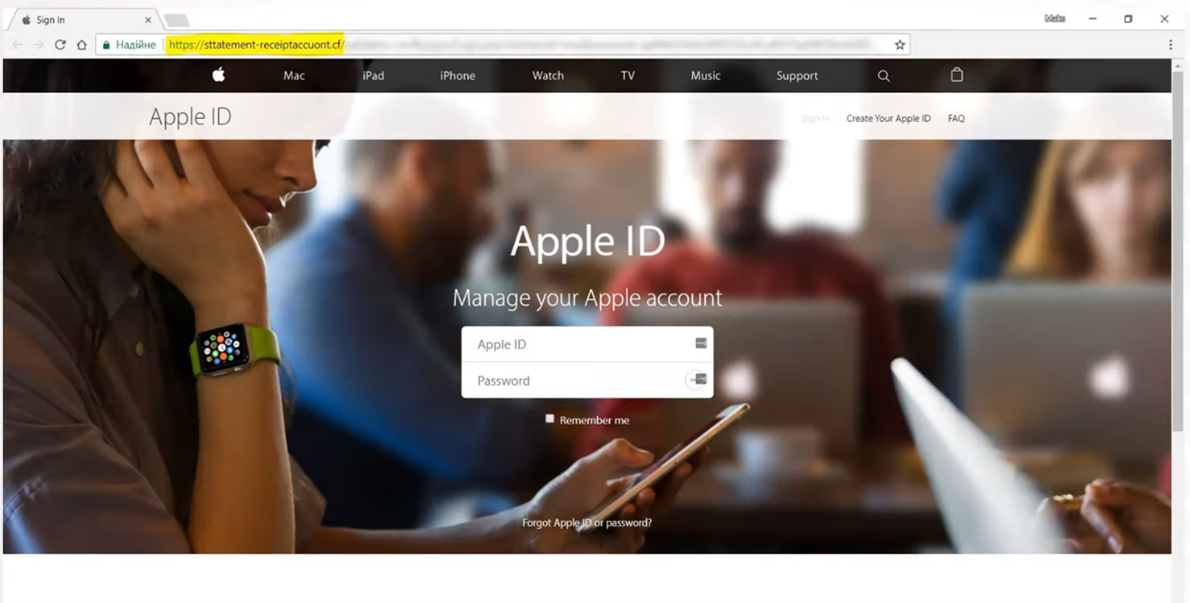
How to check files for viruses?
- Save file but DO NOT open it
- Open Virustotal.com website
- Upload file to be reviewed
- View antivirus scan results
Protecting accounts from hacking
- Account being registered on trusted mail address
- Use unique passwords for important accounts
- 2-Step Verification (SMS/generator/backup codes) should be configured
- Use the account only on your devices
- Customized ways to restore access to your account or securely saved password
Communication protection
- Do not say anything secret on your mobile phone
- Do not write anything secret in SMS
- It is safer to talk over the Internet
- Facebook Messenger, Telegram, Skype
- WhatsApp, Signal, Telegram secret chat
- Protect devices
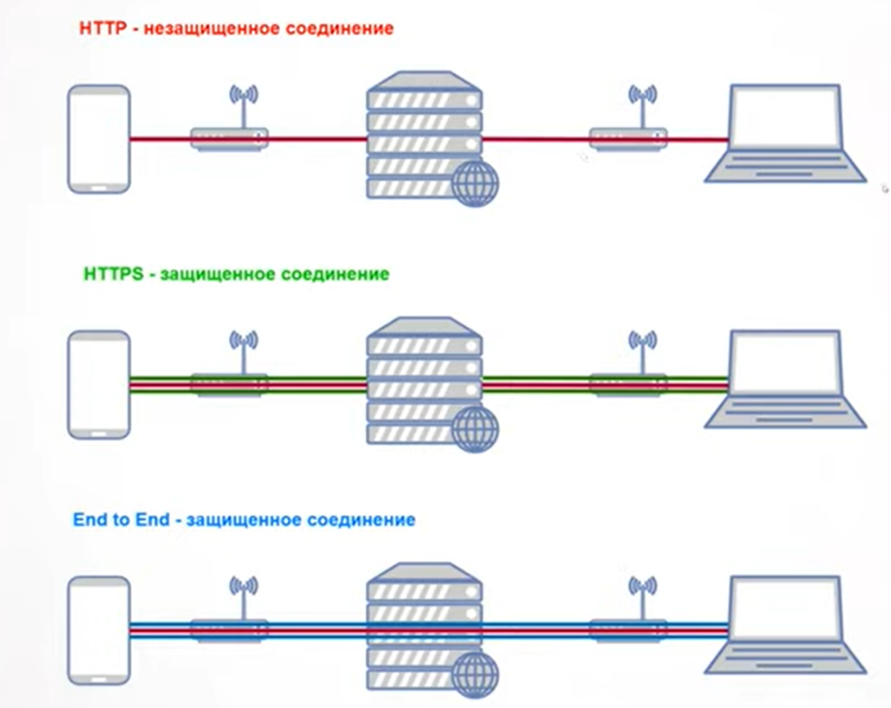
Possible risks with devices
- Breakage, theft, loss of device and loss of information
- Virus infection, leaking or loss of information
- Withdrawal and subsequent access to information
Computer protection
- Use of legal operating systems and programs
- Regular software updates
- Back up important data
- Account separation in Windows or MacOS
- Lock with password
- If you need protection against seizure and access to data, encrypt
Mobile Device Protection
- Latest versions of Android OS or iOS
- Regular software updates
- Back up important data
- Screen lock with password/pin code/bio-metrics
- Hidden message content on locked device
- If you need protection against seizure and access to data, encrypt
- Do not give the phone to anyone

8 simple principles which can help you to distinguish truth from fake news
- The primary principle is to distrust all sources of information. Choose one source with a transparent information policy and a good news service that you really trust.
- Now expand the list of sources, guided, as in the primary principle, by common sense and using the following tips:
- a team is better than one person
- better an independent team whose work is paid by readers
- clearly defined anti-war position
- Select at least two to a maximum five sources, taking into account the time the information resource appeared (you should be wary of the newly created and unknown onces), and whether and if so, which personnel changes took place lately in the information resource you’ve selected.
- Ignore official sources, media with state participation. For example, the requirement of Roskomnadzor to use only information from Russian official sources when covering the war topic, is de facto military censorship.
- When it comes to infrastructure, read the primary sources. Information about flight cancellations should be taken from the airport website, about the injection of money into the economy by the Central Bank – from the press release of the Central Bank, etc.
- Don’t get emotional and keep cool. Try to avoid news with value judgments of the authors (“their vile spies”, “our brave scouts”, etc.).
- Social networks and instant messengers are unreliable. Especially in wartime, trolls who are given content plans about what and how to write become active, as well as coordinated campaigns are being organized to spread lies. You should ignore not only the messages in your feed, but also in the comments under your posts.
- Don’t be afraid to miss something. By following the informational diet described above, you will have more time for positive creativity and reflection.
